Application Management
Creating an Elastic Beanstalk Application
Most applications are deployed using Elastic Beanstalk and made available through Cloudfront. You must first create an application in the Elastic Beanstalk console, and then create an environment within that application, which is configured as follows:
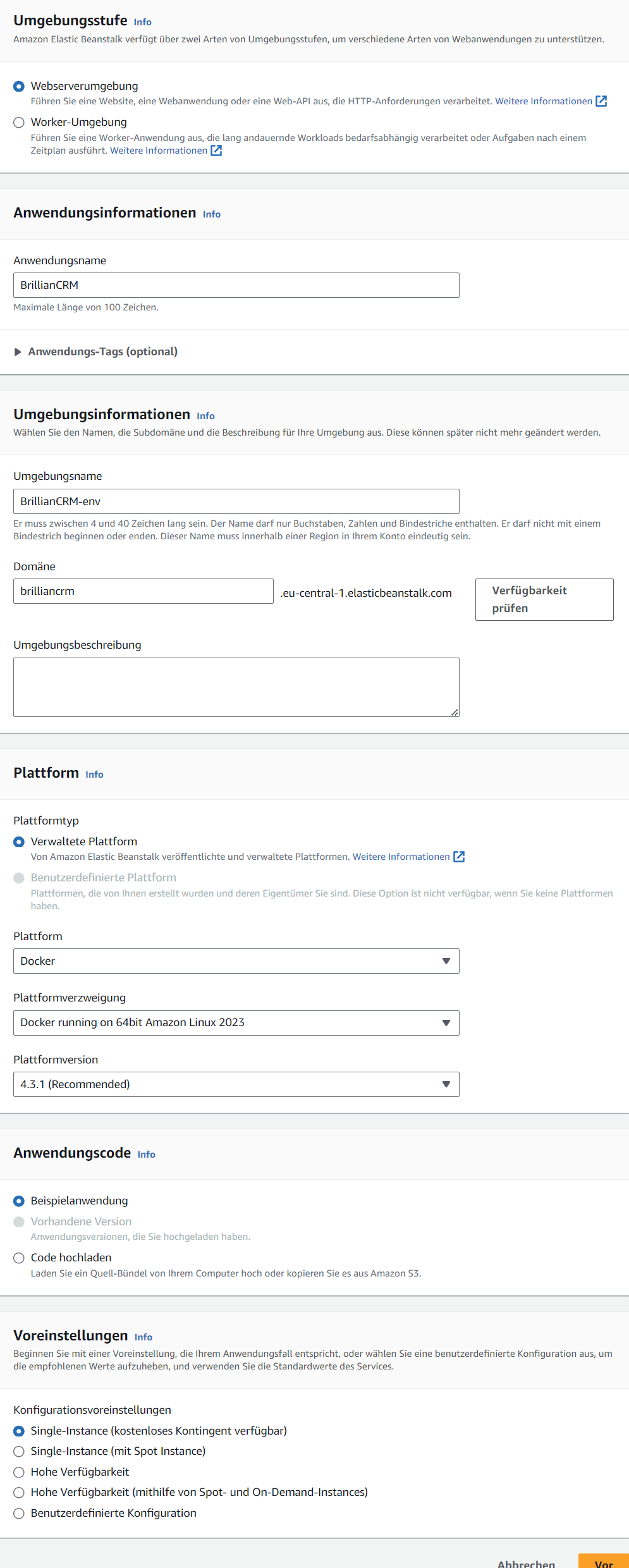
Step 1: Konfigurieren der Umgebung
- Select a name for the application (
BrillianCRM) and environment (BrillianCRM-env), then select the Elastic Beanstalk domain (brilliancrm.eu-central-1.elasticbeanstalk.com), which is later required for the integration with AWS CloudFront. The application and environment name must match the one defined in thedeploy-AWS.ymlGitHub workflow. - Set the platform to Docker and leave the other platform options at default.
- Select
sample applicationfor the initial deployment. The actual code will be automatically uploaded later via GitHub. Note that after deployment, it is also possible to manually upload adocker-compose.ymlfile directly from the AWS Beanstalk GUI. - Pick
Single-Instance (kostenloses Kontingent verfügbar).
Screenshot: Step 1
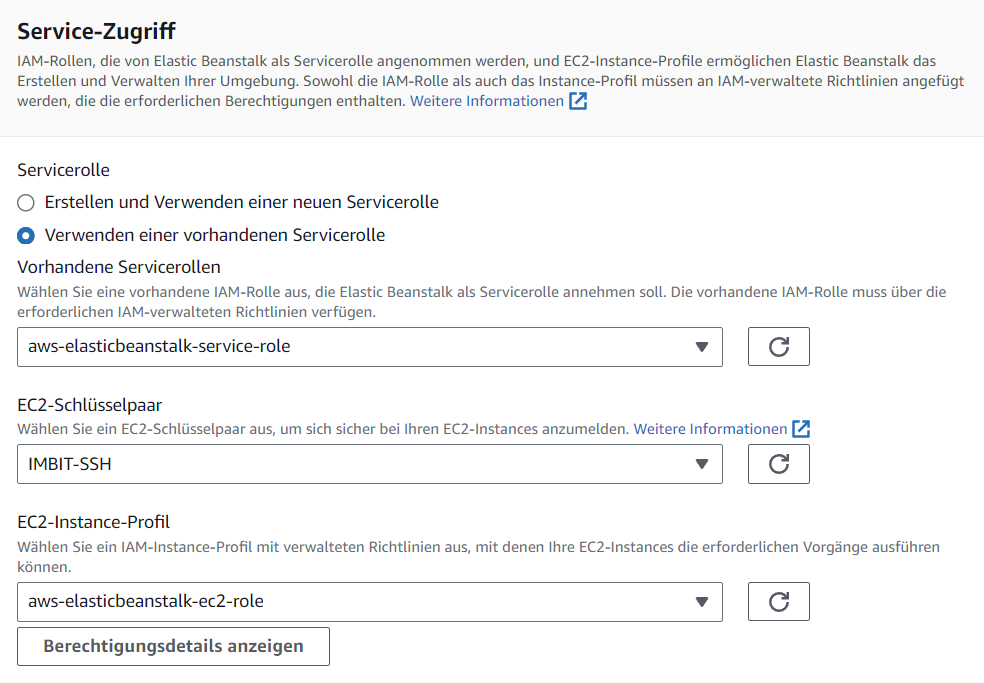
Step 2: Konfigurieren des Servicezugriffs
- Pick
Verwenden einer vorhandenen Servicerolle. - Service role:
aws-elasticbeanstalk-service-role. - EC2 SSH key pair:
IMBIT-SSH. - EC2 instance profile:
aws-elasticbeanstalk-ec2-role.
Screenshot: Step 2
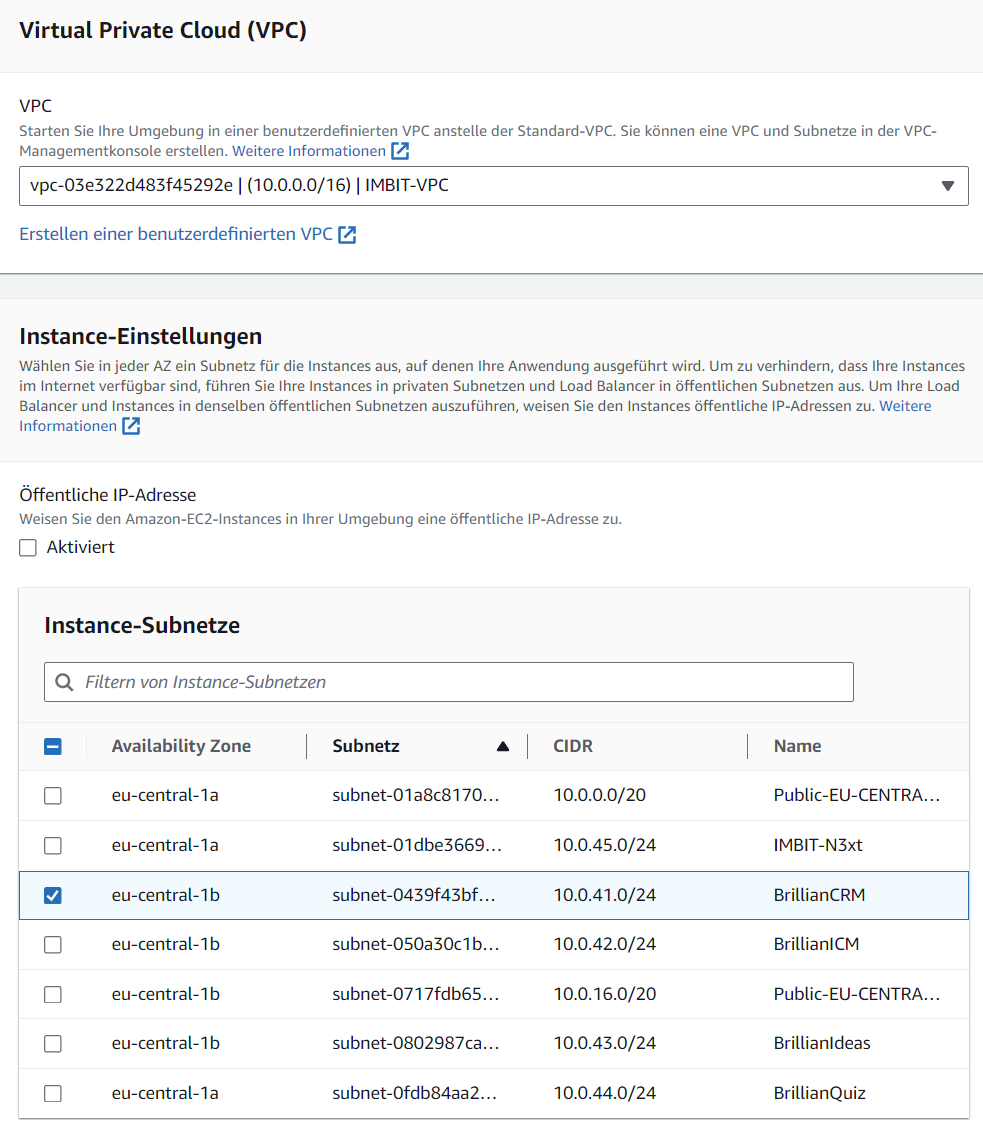
Step 3: Einrichten von Netzwerk, Datenbank und Tags
- Select
IMBIT-VPCfor the VPC. - Do not assign a public IP, but add the application to its own subnet. Please give each application its own subnet, as they should all get their own subnet for proper security! Read more about AWS Networking.
- No associated databases and tags are configured.
Screenshot: Step 3
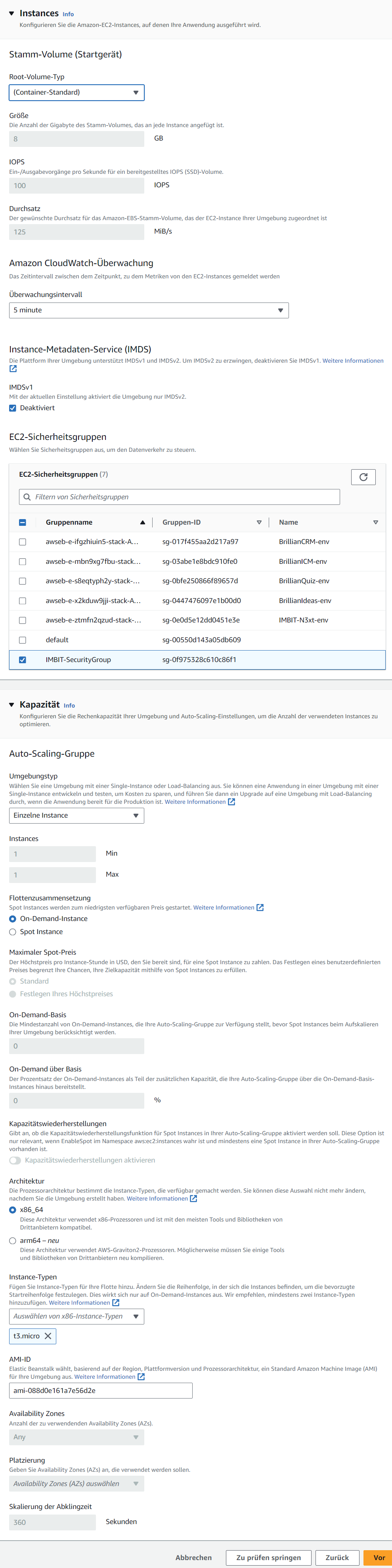
Step 4: Konfigurieren des Instance-Datenverkehrs und der Skalierung
- Keep the default settings for the volume
Container-Standard, CloudWatch interval5 minuteand IMDSv1. - Add the EC2 security group
IMBIT-SecurityGroup. - Our applications are not configured to scale, leave the default
Einzelne InstanceandOn-Demand-Instancesetting. - In terms of architecture,
ARM64can be chosen for cost efficiency, but compatibility with the code base should be checked (only theBrillianIDEASapplication is known to work withARM64). - The smallest instance with 1 GB RAM should suffice, as of 2024 that would be for ARM64
t4g.microand for x86_64t3.micro. More on AWS Instances.
Screenshot: Step 4
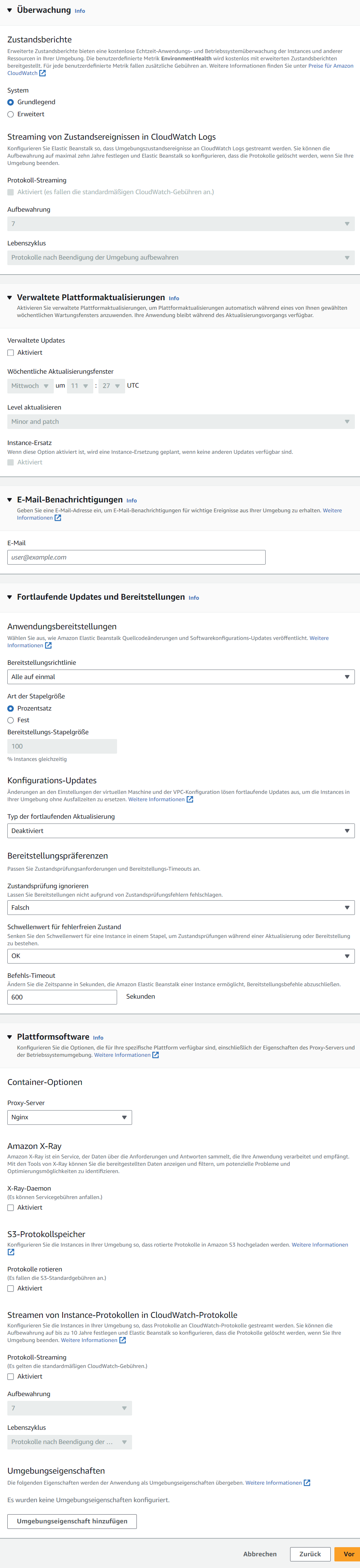
Step 5: Konfigurieren von Updates, Überwachung und Protokollierung
- Set Health reporting to basic.
- Disable automatic updating, as it has crashed in the past. However, it may be worthwhile to re-evaluate and test automatic updates in the future.
- Leave all other settings at default.
Screenshot: Step 5
Step 6: Prüfen
- Review the summary for errors and apply.
- After about 5 minutes, the application will be accessible via its Elastic Beanstalk URL and it should show the AWS sample application.
- Now you can update the application using the GitHub workflow.
CloudFront as a Reverse Proxy
AWS CloudFront acts as a reverse proxy, and per Beanstalk application one CloudFront deployment is required.
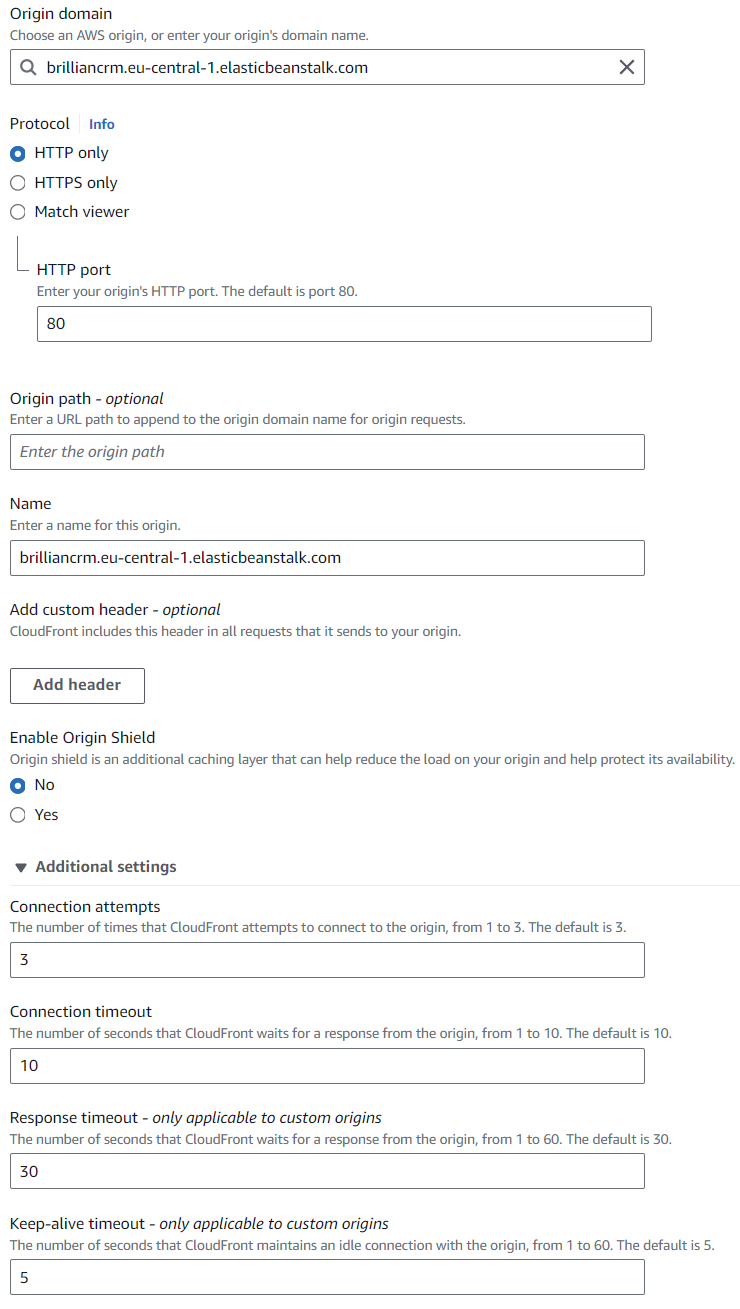
Origin Settings
- The origin domain is configured using the URL of the Elastic Beanstalk application (
http://brilliancrm.eu-central-1.elasticbeanstalk.com). - Set the protocol to
HTTP onlyand on port80. Elastic Beanstalk applications will only have this port and protocol open. - Origin path is left empty, but adjust it if your application requieres it.
- The Origin name is set to the name of the application (
BrillianCRM). - Leave the other origin settings as default.
Screenshot: Origin Settings
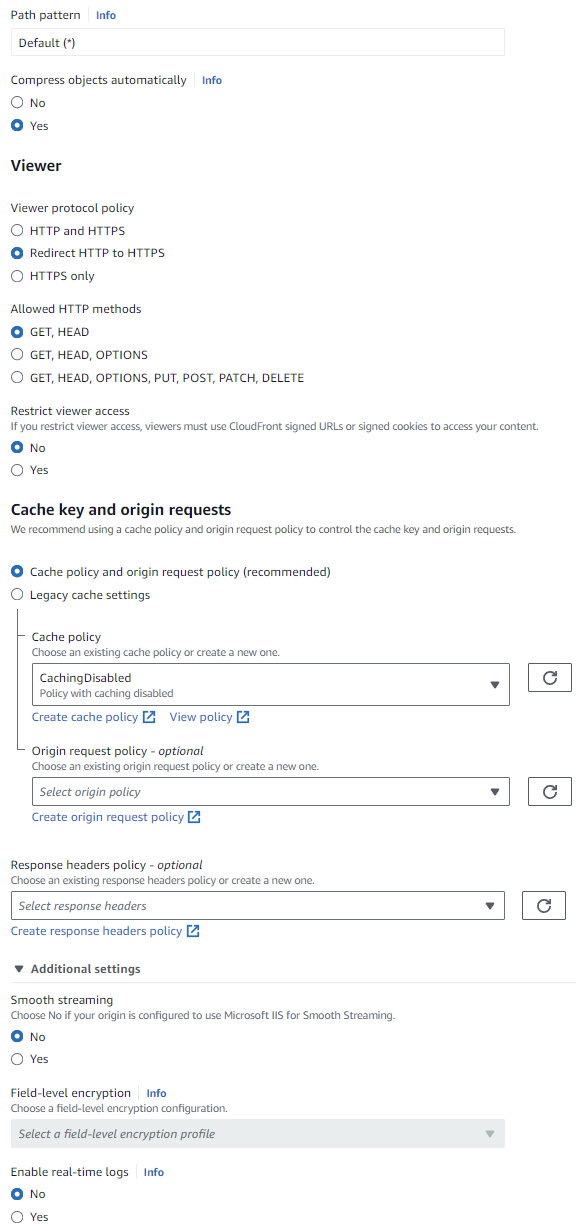
Default Cache Behavior
- Leave most settings at their default values, unless otherwise noted here. See the Screenshot below for more details.
- Select
Redirect HTTP to HTTPSfor the Viewer protocol policy. - Standard HTTP methods (
GET, HEAD) usually work, however BrillianCRM, ICM and QUIZ requireGET, HEAD, OPTIONS, PUT, POST, PATCH, DELETEfor user login to work. - Caching policy
CachingDisabledis chosen as otherwise it takes some time for changes to go live.
Screenshot: Default Cache Behavior
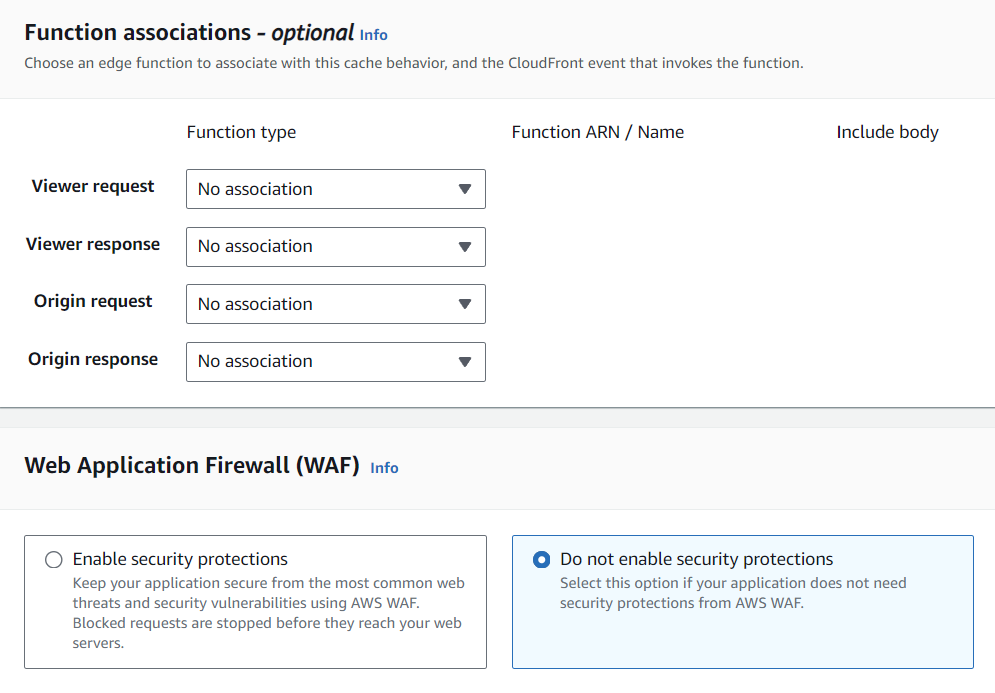
Function associations and Web Application Firewall (WAF)
- No function associations are created.
- Disable the WAF to save costs.
Screenshot: Function associations and Web Application Firewall (WAF)
Settings
- Select for the Price class
Use only North America and Europeto reduce costs. - To enable CloudFront to respond to requests for custom domains, such as
brilliancrm.com, alternative domain names need to be entered.- Press
Add itemfor each entry. - Enter the base URL (
brilliancrm.com). - Add the base URL with the www-prefix (
www.brilliancrm.com).
- Press
- Leave the other settings at their default values.
Screenshot: Settings
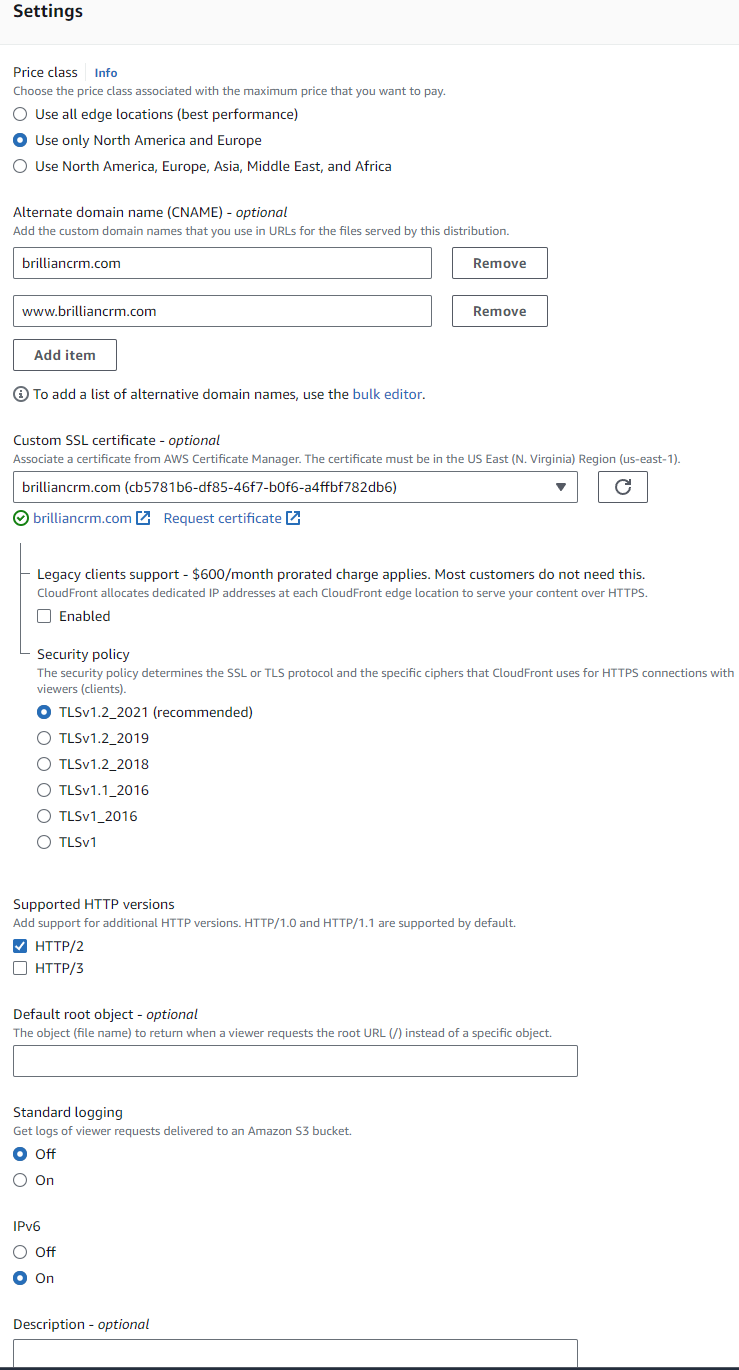
- CloudFront automatically provides HTTPS if custom domain SSL certificates are selected. Please select the appropriate certificate. The certificates can be requested in AWS ACM (Certificate Manager) [North Virginia region!].
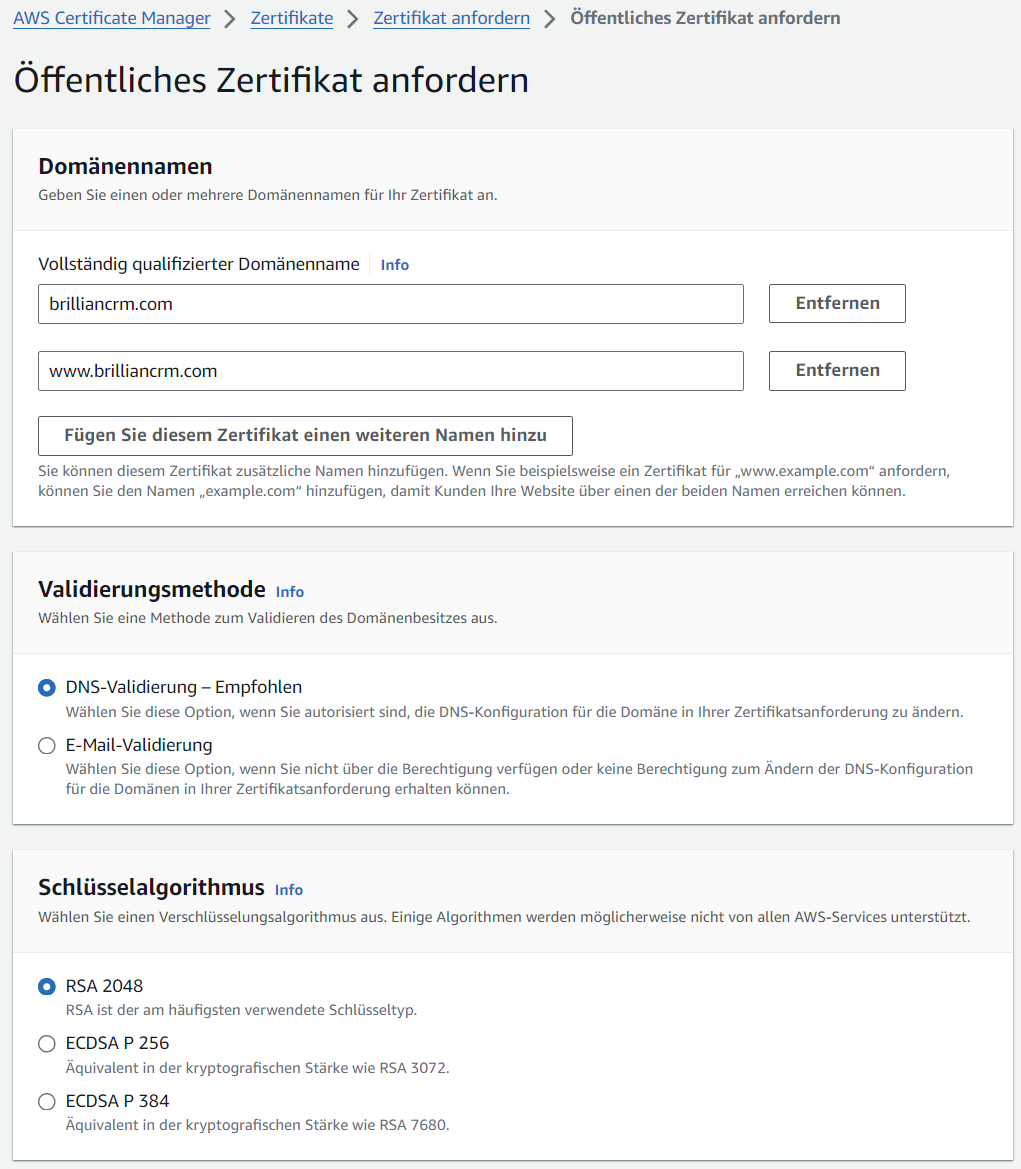
- When setting up SSL certificates with AWS ACM, the domain name and its
wwwsubdomain must be included in the request.Screenshot: Certificate Request
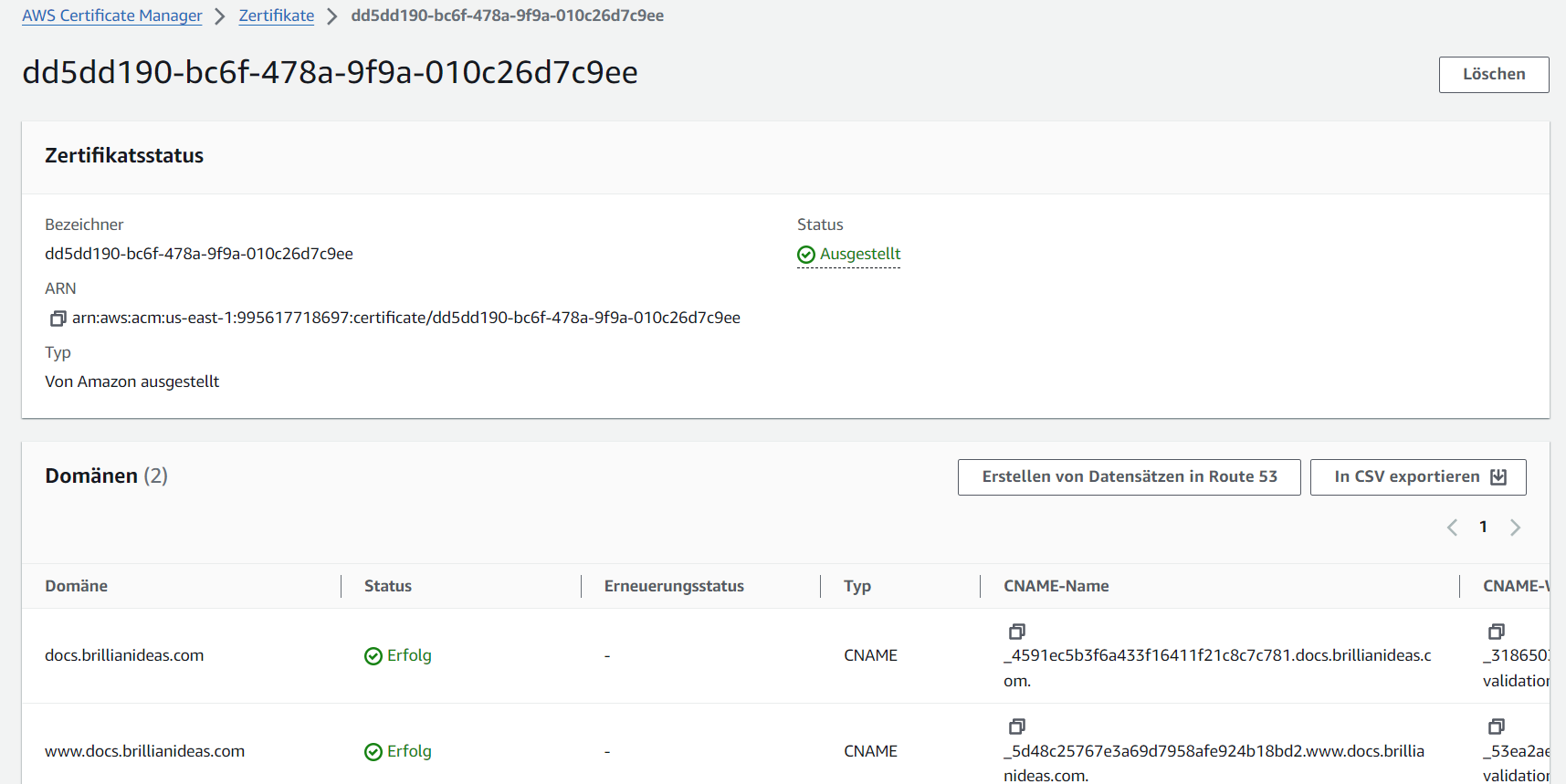
- Validation is performed using CNAME records. The records must be created by clicking on the Certificate ID and clicking the
Erstellen von Datensätzen in Route 53button.Screenshot: Create DNS Records for certificate validation
- When setting up SSL certificates with AWS ACM, the domain name and its
Activating the CloudFront Distribution
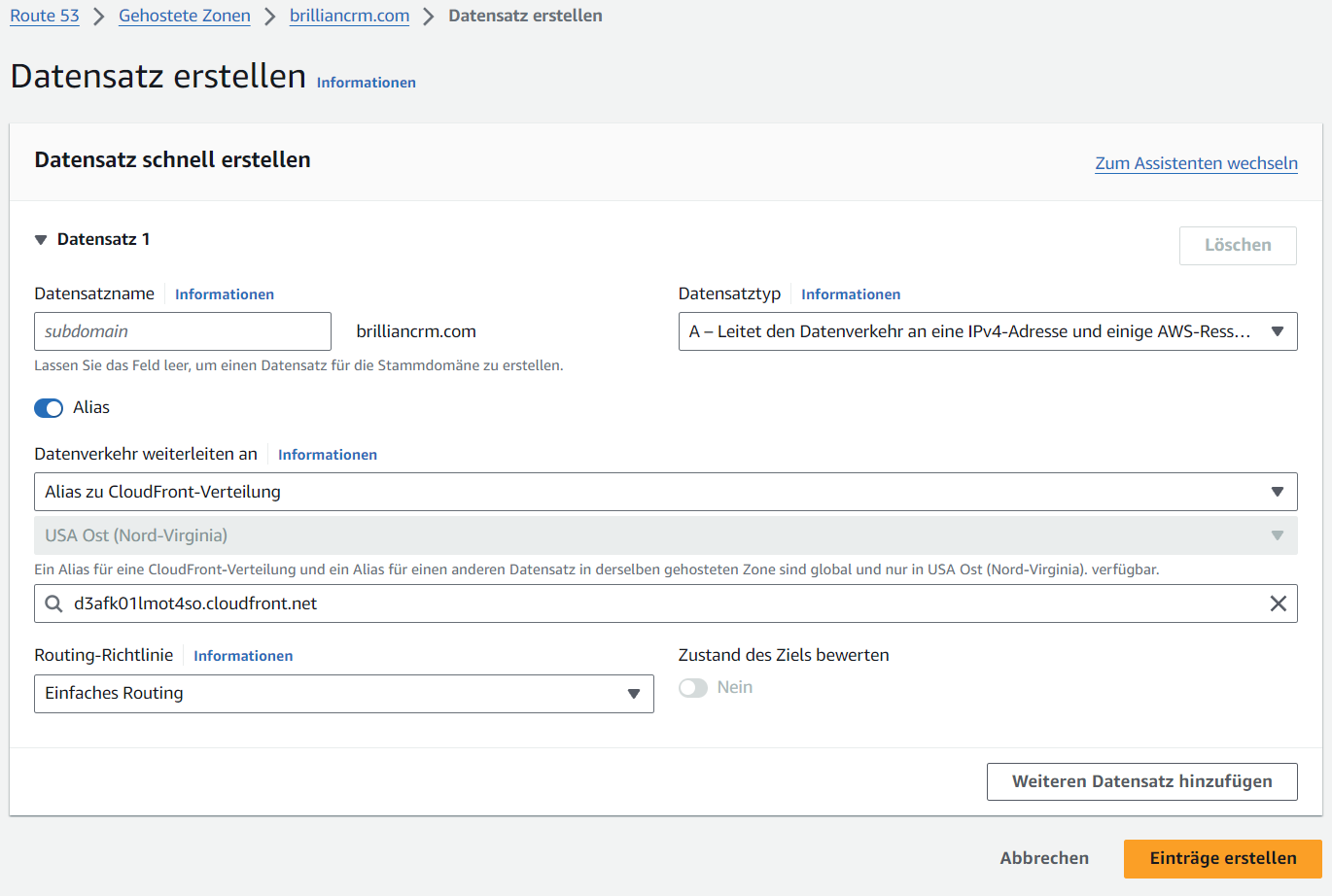
- It takes some time to deploy the CloudFront distribution, once done the distribution gets a CloudFront URL (
d3afk01lmot4so.cloudfront.net). - In Route 53, select the domain and create a new DNS record.
- Enable the
Aliastoggle and leave the DNS type asA. - Select
Alias to CloudFront distribution, paste in the field below the CloudFront URL and create the DNS record. - Allow some time for the DNS changes to propagate and you are done.
Screenshot: DNS Record Creation
Stop or Remove an Application
Potential Data Loss
Before stopping an application, please be aware of the data loss potential.
- Applications can be stopped and removed from the Elastic Beanstalk dashboard. The status of the application will update to
beendetand will be automatically removed by AWS after a period of time. - To remove a Cloudfront distribution, you must first stop it, wait, and then you can remove it.
- Don't forget to remove the DNS records in Route 53 and delete the certificates in ACM.